The Melissa virus, discovered in March 1999, ranks as one of the most damaging macro viruses in history. Its rapid proliferation underscores the importance of robust digital security measures. This virus rapidly propagated through email systems, disguising itself as an innocent document, leading to significant disruptions across the globe. Its impact on devices was both immediate and profound, causing widespread damage and highlighting the need for robust cybersecurity measures.
What is the Melissa Virus
The Melissa virus was created by a man named David L. Smith, who distributed it via email disguised as a Microsoft Word document titled “Important Message from [Sender’s Name]”. This social engineering tactic enticed users to open the attachment and unknowingly activate the virus.
Once opened, the virus would email itself to 50 contacts in the user’s address book, leading to its rapid spread. It also could corrupt files, causing system crashes and potentially deleting important documents.
How Did it Affect Businesses and Individuals
The Melissa computer virus caused significant disruption to businesses and individuals, resulting in an estimated $80 million in damages. Many large companies were forced to shut down their email systems to contain the virus, resulting in significant financial losses.
The virus also caused personal computers to crash and delete important files, distressing and frustrating individuals. The widespread impact of the virus highlighted the vulnerability of digital systems and the need for effective cybersecurity measures.
How Can You Defend Against Melissa Virus
To effectively combat threats like the Melissa virus that caused extensive damage and exposed computer vulnerabilities, adopting a multifaceted cybersecurity approach is crucial. This involves installing and updating antivirus software, educating users about safe email practices, and regularly backing up data for comprehensive protection against malicious attacks.
Update Antivirus Software Regularly
Keeping antivirus software up-to-date with the latest virus definitions is crucial in protecting against viruses like Melissa. The software will be able to detect and block the virus before it can cause any damage.
Enable Email Filters
Email filters can help prevent malicious emails, such as those containing the Melissa virus, from reaching your inbox. These filters can also flag suspicious attachments or links that may contain viruses.
Watch out for Suspicious Emails
Similar to the Melissa virus incident; deceptive methods are commonly employed to deceive individuals into opening infected attachments. Exercise caution with emails from unfamiliar sources or those with vague subject lines.
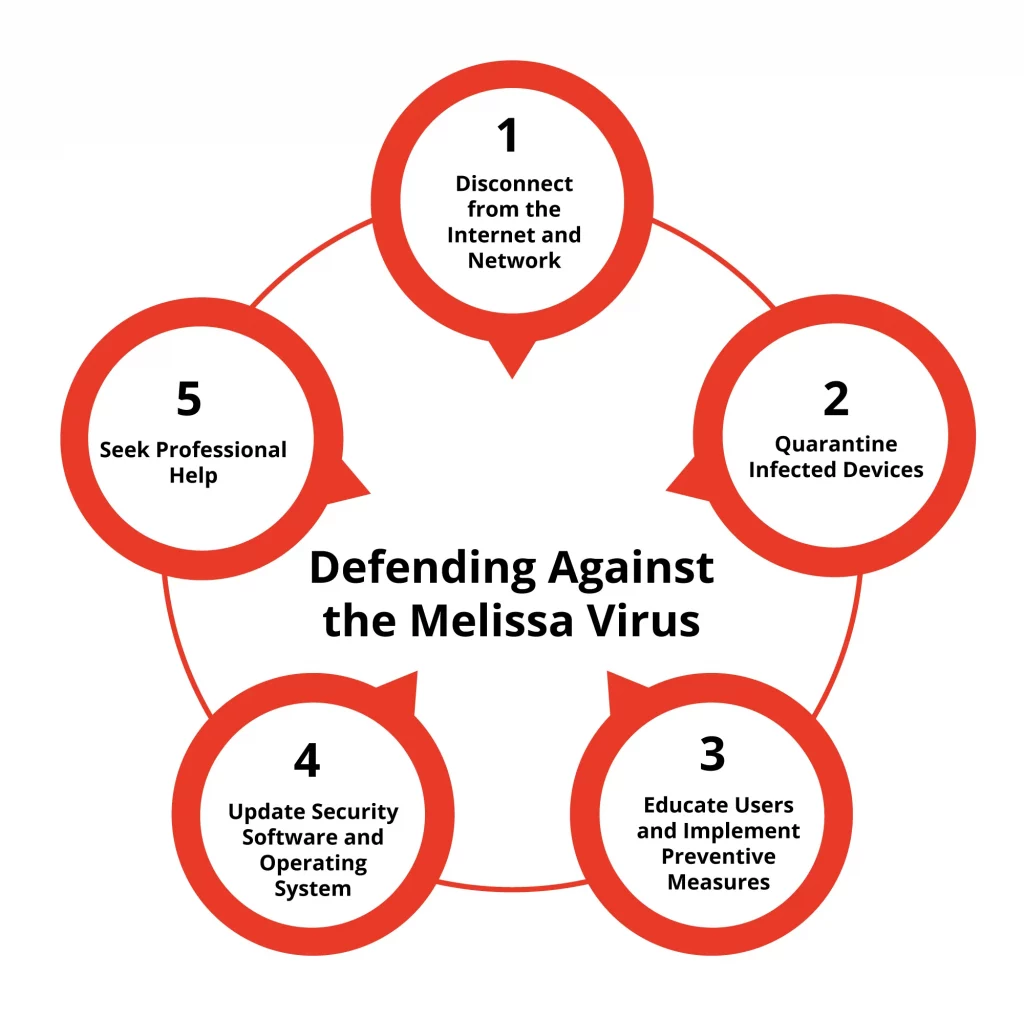
Disable Macros in Microsoft Office
The Melissa virus was a macro virus, meaning it used macros within Microsoft Word to infect computers. By turning off macros in your Microsoft Office settings, you can prevent potentially harmful macros from running.
Back up Important Files
In the event that a virus like Melissa does cause damage to your system or files, having regular backups of important documents will ensure that they can be recovered.
Building a Strong Cybersecurity Culture
While implementing security measures is crucial in defending against viruses like Melissa, building a strong cybersecurity culture within organizations and among individuals is equally important. By working together to prioritize digital security, we can better protect ourselves and our businesses from malicious attacks like the Melissa virus.
This includes regular training and education on safe digital practices, enforcing strong password policies, and staying informed about the latest cyber threats.
In conclusion, the Melissa virus served as a wake-up call for the importance of strong cybersecurity measures and highlighted the need for constant vigilance in defending our digital domains.
By staying educated and implementing proper security measures, we can better protect ourselves from such damaging viruses in the future. The Melissa virus was a significant wake-up call for individuals and businesses to prioritize cybersecurity.
Getting Professional Help to Defend Against Melissa Virus
Suppose the Melissa virus infects your devices, and you cannot access your data. In that case, it is crucial to contact professional data recovery services immediately to prevent further data loss. Contact our expert technicians immediately for personalized assistance and to regain access to your lost files. Our skilled team utilizes cutting-edge technology and extensive knowledge to recover data affected by the computer virus Melissa or other malware.
FAQ about Defending Against the Melissa Virus
Is it the Melissa virus or worms?
The Melissa virus is a macro virus, not a worm. It spread through email, infecting computers via Microsoft Word macros. Once triggered, it replicated by emailing the first 50 contacts in a user’s Outlook address book, spreading rapidly. Melissa needed user action, like opening an infected attachment, to spread. This highlights the critical need to understand different malware types and their behaviours, such as the key differences between viruses and worms.
Why is backing up data important for cybersecurity?
Regular backups ensure that your important files can be recovered without paying ransom or losing critical information in the case of a cyberattack or data loss. For maximum security, backup data in multiple locations, including cloud storage and external drives.
What should I do if I think my computer is infected?
Disconnect your computer from the Internet to prevent the virus from spreading. Run a full system scan with your antivirus software, and consider seeking professional help if the virus persists or you can’t remove it.
How can you determine if an email is malicious?
Suspicious emails often include generic greetings, urgent or threatening language, misspellings, and requests for personal information. Always make sure to check the email sender’s address before opening attachments or clicking on links from unknown sources.
What are macro viruses?
Macro viruses are a type of malware that infects documents and spreads by exploiting the macros feature in productivity software like Microsoft Word. These viruses can perform a series of unwanted actions, from corrupting data to sending themselves through email.
