In the ever-evolving landscape of cyber threats, one name that has gained notoriety is Maktub Ransomware. This malicious software, often referred to as Maktub Locker, has wreaked havoc on local networks and individual systems worldwide. In this blog post, we will delve into the world of Maktub Ransomware, exploring its origins, its methods of infection, and, most importantly, strategies to safeguard your data from falling victim to this insidious threat.
Origins of Maktub Ransomware
Maktub Ransomware first emerged on the cybercrime scene around 2014. Its name, “Maktub,” is derived from an Arabic word that translates to “it is written.” Just like its name implies, the presence of this ransomware on your system can feel preordained, as once it infiltrates your network, it can encrypt your files with ruthless efficiency.
Infection Methods: The Role of Phishing Emails
Maktub Ransomware, like many other forms of malware, relies heavily on phishing emails as a primary infection vector. These malicious emails are cunningly crafted to deceive recipients into taking an action that invites the ransomware onto their systems. Common tactics include:
- Social Engineering: Attackers often use psychological manipulation to craft convincing messages. These emails might impersonate legitimate organizations, friends, or colleagues, making them appear trustworthy.
- Malicious Attachments: Maktub Ransomware is typically delivered through malicious attachments in these emails. These attachments may contain infected documents or links to compromised websites.
- Exploiting Vulnerabilities: In some cases, the ransomware exploits software vulnerabilities to infect systems directly when the user opens an email or views an email attachment.
The Encryption Process
Once Maktub Ransomware infiltrates a system, it swiftly moves to encrypt files, rendering them inaccessible to the victim. The encryption process is a key element of the ransomware’s operation, and it happens at remarkable speed to maximize the impact on the victim.
- Selection of Targeted Files: Maktub Ransomware typically targets a wide range of file types, including documents, images, videos, and more. This comprehensive approach ensures that victims are left with little choice but to comply with the attackers’ demands.
- Speeding up the Encryption: Maktub Ransomware is known for its efficiency in the encryption process. It uses strong encryption algorithms to lock files securely. This means that once the process starts, there is very little time to react before files become inaccessible.
Demands and Terms of Service
After encrypting the victim’s files, Maktub Ransomware displays a ransom note on the infected computer screen. This note contains the attackers’ demands and instructions on how to pay the ransom to receive a decryption key. The ransom demands can vary widely, ranging from a few hundred to several thousand dollars, with payment often required in cryptocurrencies like Bitcoin to maintain anonymity.
It’s important to note that complying with the ransom demand is highly discouraged by law enforcement agencies and cybersecurity experts. Paying the ransom does not guarantee that you will receive a working decryption key, and it only fuels the criminal activities of the attackers.
How to Protect Against Maktub Ransomware?
Now that we have a clearer understanding of Maktub Ransomware let’s explore strategies to protect your local network and data from falling victim to this threat:

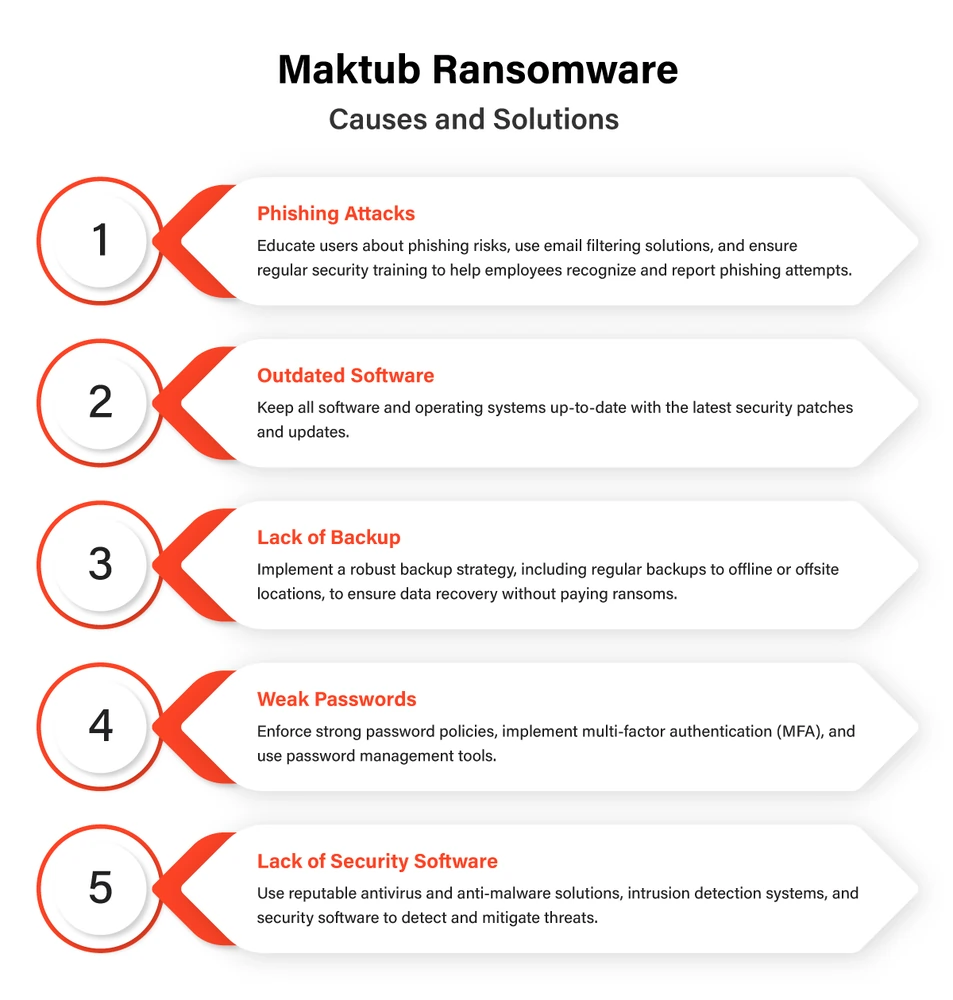
1. Robust Anti-Virus and Anti-Malware Software
Invest in reputable anti-virus and anti-malware software for all devices in your network. Regularly update these programs to ensure they can detect the latest threats, including Maktub Ransomware, and promptly remove them.
2. Employee Training and Awareness
Educate employees and network users about the risks of phishing emails and the importance of exercising caution when opening attachments or clicking on links in emails. Regularly conduct phishing awareness training to enhance their ability to recognize malicious emails.
3. Email Filtering and Security
Implement robust email filtering and security solutions that can identify and block phishing emails before they reach users' inboxes. These solutions use advanced algorithms and threat intelligence to identify malicious content.
4. Regular Backups
Frequently back up your data to secure, offline storage locations. In the event of a ransomware attack, having up-to-date backups will allow you to restore your files without paying a ransom.
5. Network Segmentation
Segment your network to limit the lateral movement of ransomware within your organization. By isolating critical systems and data, you can contain an infection and prevent it from spreading to other parts of your network.
6. Incident Response Plan
Develop a comprehensive incident response plan that outlines the steps to take in the event of a ransomware attack. Ensure that all employees are aware of the plan and know their roles in the event of an incident.
7. Cybersecurity Partnerships
Consider partnering with cybersecurity experts and organizations to enhance your network's security posture. Collaborative efforts can help you stay updated on emerging threats and best practices.
Maktub Ransomware remains a persistent and evolving threat in the world of cybersecurity. Understanding its origins, infection methods, encryption process, and the demands it makes is essential for protecting your local network and data. By implementing robust cybersecurity measures, including anti-virus software, employee training, email filtering, and regular backups, you can significantly reduce the risk of falling victim to this malicious software. Remember, vigilance and preparedness are your best defenses against the ever-present threat of ransomware.
Frequently Asked Questions
What is Maktub Ransomware?
Maktub Ransomware, also known as Maktub Locker, is malicious software designed to encrypt the files on a victim’s computer or network. Once files are encrypted, the attackers demand a ransom in exchange for a decryption key to unlock the files.
How does Maktub Ransomware infect computers?
Maktub Ransomware primarily infects computers through phishing emails. Attackers send deceptive emails with infected attachments or links that, when clicked, can download and install the ransomware on the victim’s system.
What happens to my files when they are encrypted by Maktub Ransomware?
When Maktub Ransomware encrypts your files, they become inaccessible. Each encrypted file is locked with a strong encryption algorithm, and you’ll need a decryption key, typically held by the attackers, to regain access to your files.
How can I protect my computer or network from Maktub Ransomware
To protect against Maktub Ransomware, regularly update your anti-virus and anti-malware software, educate yourself and your employees about phishing threats, use email filtering systems, maintain up-to-date software with security patches, and regularly back up your data to offline storage. Having a robust cybersecurity plan is essential for prevention and response.