In the chilling world of cybersecurity, new threats emerge constantly, and one of the most dreaded among them is Jigsaw ransomware. Named after the infamous puppet from the horror movie series “Saw,” this malicious software targets unsuspecting victims, encrypts their files using AES encryption and demands a ransom for their release. In this blog post, we will delve into the horrors of Jigsaw ransomware, exploring its methods of infection, understanding its impact, and learning how to safeguard ourselves against this nightmarish threat.
What is Jigsaw Ransomware?
Jigsaw ransomware is a vicious malware strain designed to terrorize individuals and organizations alike. Like its movie namesake, Billy the Puppet, it seeks to instil fear and anxiety in its victims by threatening to delete their files unless a ransom is paid. First discovered in 2016, Jigsaw has since undergone several evolutions, with newer variants becoming even more sophisticated and difficult to detect.
How Jigsaw Ransomware Infects Devices?
Jigsaw typically enters a system through common ransomware attack vectors, such as malicious email attachments, infected downloads, or compromised websites. Once it infiltrates a device, the nightmare begins. The ransomware starts by encrypting files using the advanced AES encryption algorithm, making them inaccessible to the user. It then proceeds to target the Master Boot Record (MBR) to prevent the operating system from booting properly.
The Psychological Torment: Ransom Note and Countdown
Unlike many ransomware strains that merely encrypt files and display a ransom note, Jigsaw takes psychological torment to a new level. When the infection is triggered, the victim is confronted with a haunting image of Billy the Puppet, along with a ransom note on their screen. The ransom note typically includes instructions on how to pay the ransom and a countdown timer.
What makes Jigsaw truly terrifying is the countdown timer. The ransomware threatens to delete files incrementally as the clock ticks down, increasing the pressure on the victim to pay the ransom quickly. For instance, if the victim fails to comply within the first hour, Jigsaw might delete a small number of files as a warning. Subsequent hours may witness the deletion of an escalating number of files, further coercing the victim to act hastily.
Paying the Ransom: Should You Give in to the Terror?
When faced with the nightmarish prospect of losing critical data, victims may be tempted to pay the ransom as a desperate measure to save their files. However, experts strongly advise against giving in to the demands of cybercriminals. Paying the ransom only emboldens them to continue their attacks, perpetuating the cycle of ransomware threats.

Moreover, there is no guarantee that paying the ransom will result in the safe return of the encrypted files.
Cybercriminals are notoriously untrustworthy, and there have been countless instances where victims paid the ransom, yet their files remained locked or were permanently lost during the decryption process.
Protecting Yourself Against Jigsaw Ransomware
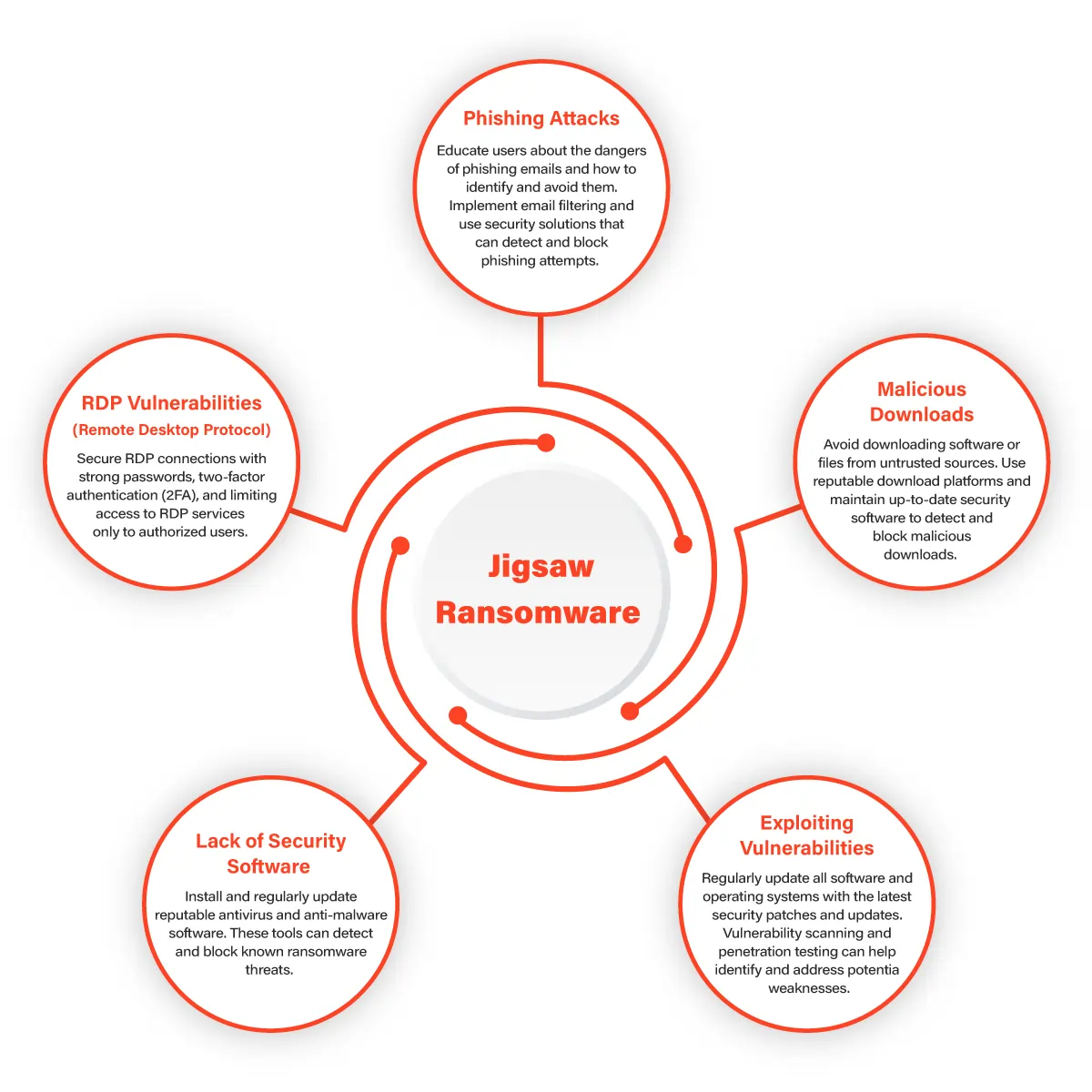
Prevention is always better than cure, and protecting yourself against Jigsaw ransomware requires a proactive approach. Here are some essential steps to safeguard your devices and data:
Backup Regularly
Implement a robust data backup strategy, storing copies of your files on an offline or cloud-based backup solution. Regular backups ensure that even if your files get encrypted, you can restore them without paying the ransom.
Keep Software Updated
Cybercriminals often exploit vulnerabilities in outdated Software to infiltrate systems. Ensure that your operating system, applications, and antivirus software are up to date with the latest security patches.
Exercise Caution with Email
Be cautious while opening email attachments or clicking on links from unknown or suspicious sources. Cybercriminals often use phishing emails to deliver ransomware payloads.
Install a Reliable Antivirus
Invest in a reputable antivirus solution that offers real-time protection against ransomware and other malware threats.
Use Ad-Blockers
Ad-blockers can prevent malicious advertisements from redirecting you to compromised websites.
Enable Firewall Protection
Activate your device’s built-in firewall to block unauthorized access.
Educate Yourself and Employees
Raise awareness about ransomware attacks among yourself and your employees if you run a business. Teach them how to spot potential threats and respond appropriately.
Jigsaw ransomware stands as a menacing figure in the realm of cybersecurity, striking fear into the hearts of its victims. With its association with the horror movie franchise “Saw,” Jigsaw leverages psychological torment and the threat of data deletion to coerce individuals and organizations into paying the ransom.
The best defense against such a horrifying threat is prevention. By following robust cybersecurity practices, backing up data regularly, and staying vigilant against potential attack vectors, we can protect ourselves from the nightmarish clutches of Jigsaw ransomware and similar malicious entities. Always remember that while cyber threats are real, so are the measures we can take to thwart them and safeguard our digital lives. Stay informed, stay secure, and together, we can face the horrors of the digital world with confidence.
Frequently Asked Questions
What is Jigsaw ransomware?
Jigsaw ransomware is malicious Software designed to encrypt files on a victim’s device, making them inaccessible. Named after the creepy puppet “Billy the Puppet” from the horror movie series “Saw,” Jigsaw terrorizes users by threatening to delete their files unless a ransom is paid.
How does Jigsaw ransomware infect devices?
Jigsaw typically enters devices through common ransomware attack vectors, such as malicious email attachments, infected downloads, or compromised websites. Once it infiltrates a system, it starts encrypting files and targets the Master Boot Record (MBR) to disrupt the operating system.
What happens if I do not pay the ransom?
If you don’t pay the ransom within the specified timeframe (usually 72 hours), Jigsaw ransomware initiates a terrifying countdown. During this countdown, the ransomware starts deleting files incrementally, adding pressure on the victim to comply. However, it is strongly advised not to pay the ransom, as there is no guarantee that your files will be decrypted even after payment.
Can I decrypt my files without paying the ransom?
In some cases, security researchers and antivirus companies may develop decryption tools to help victims recover their files without paying the ransom. It is essential to search for available decryption tools online or contact cybersecurity experts for assistance if you fall victim to Jigsaw ransomware.
How can I protect myself against Jigsaw ransomware?
To protect yourself from Jigsaw ransomware and other similar threats, follow these simple steps:
- Regularly back up your files to an external drive or a secure cloud storage service.
- Keep your operating system and Software up to date to avoid exploiting known vulnerabilities.
- Be cautious with email attachments and links, especially from unknown or suspicious sources.
- Install a reliable antivirus program that offers real-time protection against ransomware.
- Educate yourself and your employees about ransomware threats and best practices for cybersecurity.
