Ransomware attacks have become a significant threat to individuals and organizations worldwide. Among the various ransomware variants, one that has gained notoriety is BianLian Ransomware. This malicious software has caused substantial damages, including data theft and financial losses. In this blog post, we will delve into what BianLian Ransomware is, how it infects devices, and, most importantly, how you can protect yourself against this devastating cyber threat.
What is Bianlian Ransomware?
BianLian Ransomware is a highly sophisticated ransomware variant that emerged on the cyber threat landscape in recent years. The name “BianLian” is derived from a Chinese theatrical art form known as “bian lian,” where actors change their masks rapidly to portray multiple characters. Similarly, ransomware rapidly alters its tactics and techniques to evade detection and propagate its malevolent goals.
This ransomware operates on a double extortion model, where threat actors not only encrypt victims’ data but also exfiltrate sensitive information before encryption. This dual strategy puts immense pressure on victims to pay the ransom, as the threat of exposing their stolen data can lead to severe consequences, such as data breaches and reputational damage.
The BianLian Ransomware group, often referred to as the “BianLian Group,” is believed to operate out of various countries, including ones that lack strict cybercrime regulations. This allows them to conduct their illegal activities with relative impunity. Some reports suggest the group may have ties to state-sponsored actors, adding to the complexity and gravity of their attacks.
How Bianlian Ransomware Infects Devices?
The BianLian Ransomware group employs several tactics to gain access to victims’ systems. Here are some of the common methods they use:
Exploiting Vulnerabilities
The BianLian Group is known for leveraging known vulnerabilities, such as the ProxyShell vulnerability, to infiltrate vulnerable systems. They exploit these weaknesses to gain unauthorized access and install ransomware on the targeted devices.
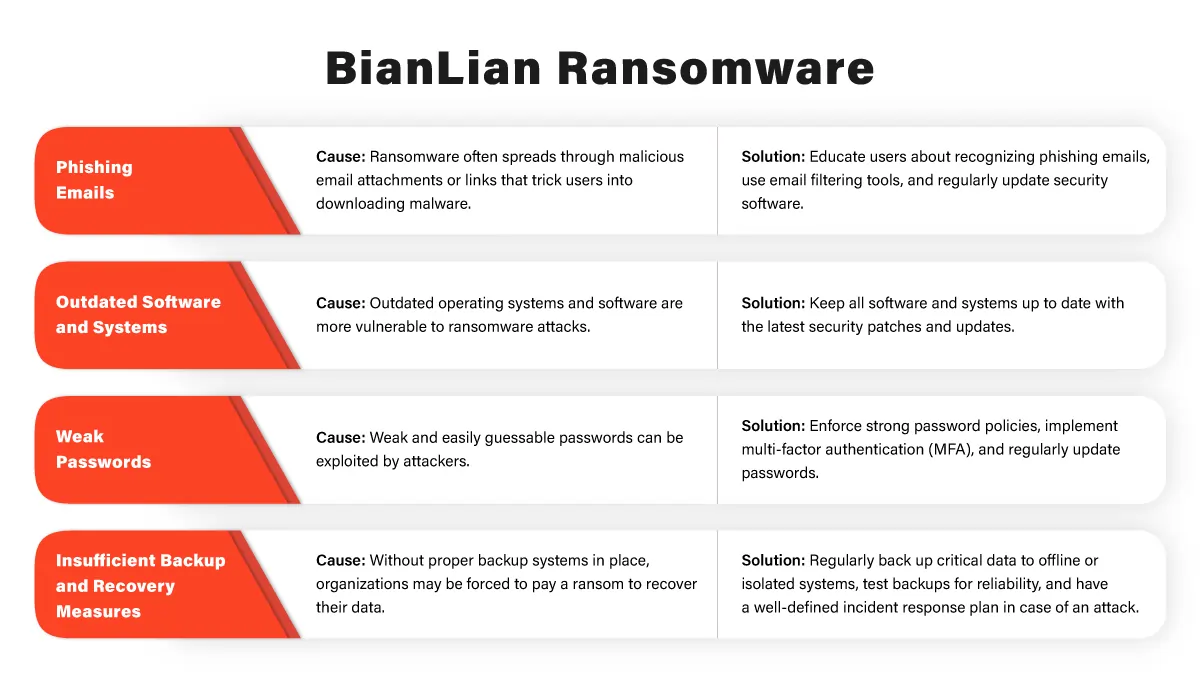
Phishing Attacks
Phishing remains one of the primary entry points for ransomware attacks. Threat actors use deceptive emails or messages to trick users into clicking on malicious links or downloading infected attachments, thereby allowing the ransomware to be deployed on the system.
Compromised Remote Desktop Services
Weak or default credentials on remote desktop services, like SonicWall VPN or other remote access tools, offer an easy path for attackers to enter a network and execute their ransomware payloads.
Malvertising and Drive-by Downloads
BianLian may also employ malvertising campaigns, where legitimate-looking ads on websites redirect users to malicious websites, leading to drive-by downloads of the ransomware.
Watering Hole Attacks
In more targeted attacks, the group might compromise websites frequented by their intended victims, using them as “watering holes” to distribute the ransomware.
Once the ransomware gains a foothold on the system, it establishes a Command and Control (C2) connection with its controllers, allowing them to manage the encryption process and data exfiltration.

Protecting Yourself Against Bianlian Ransomware
Defending against BianLian Ransomware and other ransomware variants requires a multi-layered approach to cybersecurity. Here are some essential steps you can take to protect yourself and your organization:
Regular Backups
Maintain regular backups of critical data on separate, secure storage systems. In case of a ransomware attack, having up-to-date backups will allow you to restore your data without paying the ransom.
Patch Management
Keep your software, operating systems, and applications up-to-date with the latest security patches. Regularly apply updates to mitigate the risk of known vulnerabilities being exploited by threat actors.
Employee Training
Educate your employees about ransomware attacks, phishing, and other social engineering techniques. Raise awareness about the importance of vigilant behavior and avoiding suspicious links or attachments.
Network Segmentation
Implement network segmentation to limit the spread of ransomware in case of a successful breach. This ensures that if one part of the network is compromised, the rest remains protected.
Use Multi-factor Authentication (MFA)
Enable MFA wherever possible, especially for remote access services like VPNs and remote desktops. This additional layer of security makes it harder for threat actors to gain unauthorized access.
Endpoint Protection
Invest in robust anti-malware and endpoint protection solutions to detect and block ransomware before it can execute on your devices.
Incident Response Plan
Develop a comprehensive incident response plan that outlines the steps to be taken in case of a ransomware attack. Regularly test and update this plan to ensure its effectiveness.
BianLian Ransomware is a formidable threat that poses significant risks to individuals and organizations alike. With its double extortion strategy and sophisticated tactics, the BianLian Group has caused substantial damage worldwide. Staying informed about the latest cyber threats, adopting preventive measures, and maintaining a robust cybersecurity posture is crucial to protect against this and other ransomware attacks.
By implementing a multi-layered defense strategy, conducting regular backups, and educating your employees, you can significantly reduce the likelihood of falling victim to BianLian Ransomware or any other ransomware variant.
Frequently Asked Questions
What is Bianlian Ransomware?
Bianlian Ransomware is a malicious software program designed to encrypt the files on a victim’s device, making them inaccessible until a ransom is paid. It operates on a double extortion model, where threat actors not only encrypt data but also steal sensitive information, threatening to expose it if the ransom is not paid.
How does Bianlian Ransomware infect devices?
Bianlian Ransomware employs various methods to infect devices, including exploiting known vulnerabilities, phishing attacks, compromised remote desktop services, malvertising campaigns, and watering hole attacks. These tactics allow the ransomware to gain unauthorized access to systems and execute its payload.
What is the Command and Control (C2) connection in Bianlian Ransomware?
The Command and Control (C2) connection is the communication link established between the ransomware on the victim’s device and the attackers’ servers. Through this connection, the threat actors can manage the encryption process and exfiltrate stolen data, making it crucial for their control over the attack.
Can I recover my data without paying the ransom to Bianlian Ransomware attackers?
In some cases, victims have been able to recover their data without paying the ransom by restoring from backups. Regularly backing up your data on secure systems is essential to ensure you have an alternative to paying the ransom. However, decrypting files without the attackers’ decryption key is usually not possible.
How can I protect myself against Bianlian Ransomware?
To protect yourself against Bianlian Ransomware and similar threats, follow these essential steps:
- Keep your software and systems up-to-date with the latest security patches.
- Educate yourself and your employees about phishing and social engineering techniques.
- Implement network segmentation to limit the spread of ransomware in case of an attack.
- Enable multi-factor authentication (MFA) for added security, especially on remote access services.
- Invest in robust anti-malware and endpoint protection solutions to detect and block ransomware.
